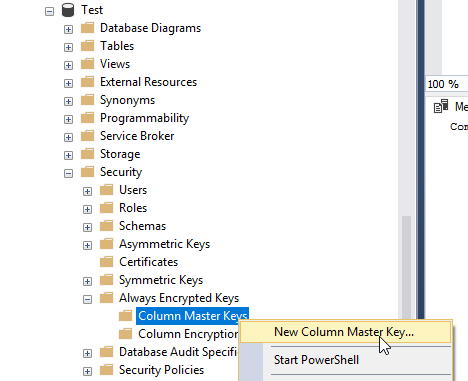
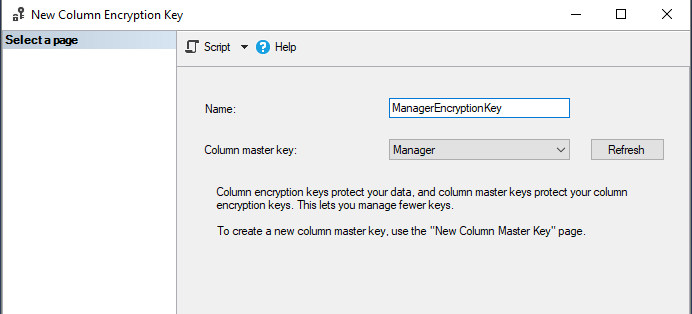
In SSMS, browse to Database, Security, Always Encrypted Keys, right click Column Master Keys and click New Column Master Key:
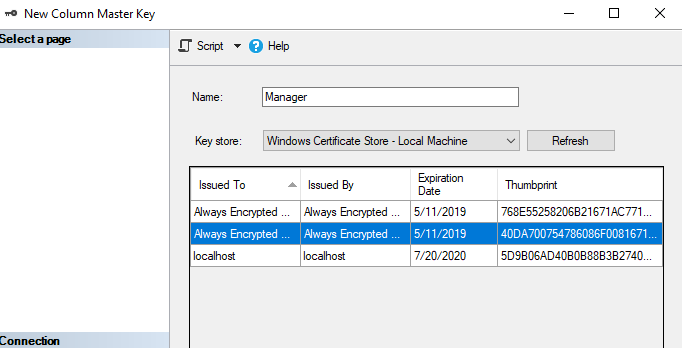
In the New Column Master Key box you can choose from several key stores. The most popular stores are Current User or Current Machine. See below for description.
Local machine certificate store
This type of certificate store is local to the computer and is global to all users on the computer. This certificate store is located in the registry under the HKEY_LOCAL_MACHINE root.
Current user certificate store
This type of certificate store is local to a user account on the computer. This certificate store is located in the registry under the HKEY_CURRENT_USER root.
Be aware that all current user certificate stores inherit the contents of the local machine certificate stores. For example, if a certificate is added to the local machine Trusted Root Certification Authorities certificate store, all current user Trusted Root Certification Authorities certificate stores also contain the certificate.
In this example, we’ll use Local Machine. Type a name for the Master Key, choose Key Store and click Generate Certificate.
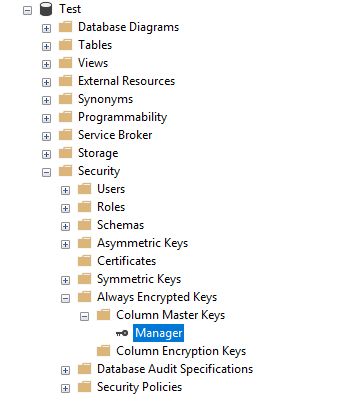
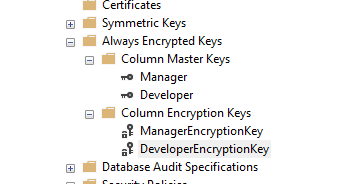
Click OK and a new Column Master Key will appear:
Do the same for any other master keys you would like to create. For example, Developer: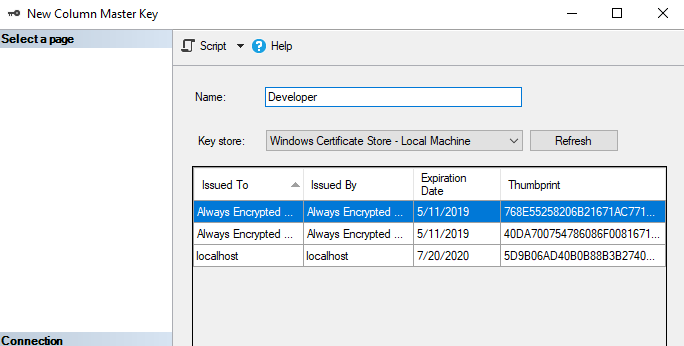
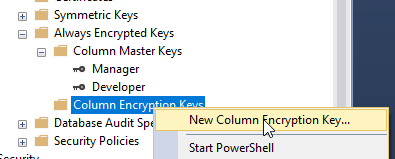
To create a Column Encryption Key, right click on Column Encryption Key and choose New Column Encryption key:
Give the key a name and select the Column Master Key that you would like to associate it with:
Do the same for the Developer keys. You should have two column master keys and two column encryption keys:
To view Local Machine certificates:
Open Certlm.msc
Browse to Personal, Certificates:
Double click a certificate and go to the Detail tab where you will see the thumbprint:
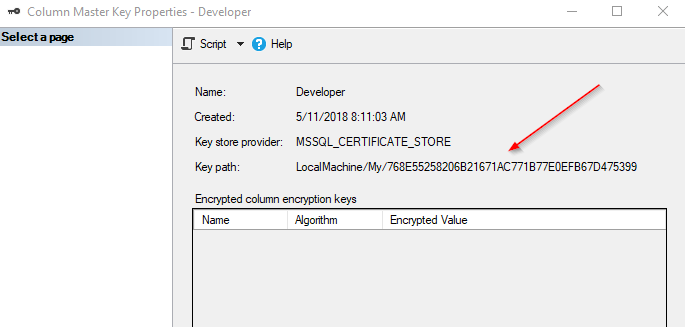
Match this thumbprint with the Column Master Key in SSMS:
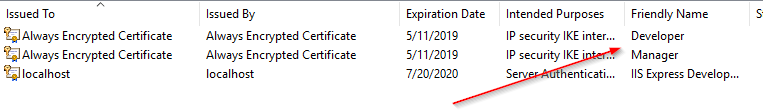
Right click the certificate in Certlm.msc and choose Properties. Enter a friendly name to identify which certificate belongs with the Column Master Key.
To Export and certificate, right click and choose All Tasks, Export: